What is DLL Hijacking and How to Prevent it?
Oct, 3rd 2023
In this article, we will explore DLL Hijacking, and how attackers use it for privilege escalation in Windows. We will also explore how to detect and prevent DLL Hijacking attacks.
But before that, and just so we are on the same page, let's start off by clarifying what a DLL is.

What is a DLL file?
Dynamic Link Libraries (DLL) are files that provide useful functions for Windows executables. Different Windows programs can load and use these functions during their execution.
To put it in simpler terms, DLLs contain code that multiple programs can use at the same time.
Using DLL files will have the advantage of reducing the application size and limiting its resource consumption. Instead of coding the same functions that programs commonly use on Windows, they can simply import them from DLL files.
As an example, the file comdlg32.dll contains common dialog box functions, like the open file box. Programs on Windows can use this already available functionality without having to code it from scratch.
What is DLL Hijacking?
DLL Hijacking is an attack technique that consists of tricking an application into loading an altered DLL file.
Under normal operation, when an application depends on a DLL file, it loads it into memory. However, a malicious actor can take advantage of this process by injecting malicious code into the DLL file. As a result, the application unknowingly executes the malicious code, altering its behavior.
If the attacker targets a program running with elevated privileges, the attack may lead to privilege escalation.
DLL hijacking can also be used to evade anti-malware detection, by leveraging a legitimate, whitelisted application to load a malicious DLL.
Furthermore, since many applications load DLL files during startup, the attacker can gain access each time the system boots. Therefore, ensuring persistence.
How to perform DLL Hijacking?
DLL file replacement is the simplest form of DLL hijacking. This is when the attacker simply replaces the legitimate file with an altered one. However, we should note that there are different approaches that adversaries may follow to conduct this attack. Here are some of the most common ones.
- Phantom DLL Hijacking: Very often, a program may depend on a missing DLL file. The attacker can insert their file at the location of the missing DLL file.
- Search Order Hijacking: When loading DLL files that are specified in relative paths, applications will try to search for the file in specific locations and following a pre-defined search order. In general, Windows will look for the file in the directory where the application was loaded. If it is not there, it will look in the system directory. And so on until it finds it. The attacker can exploit this by inserting their file at any location that is listed before the one where the legitimate file is located.
- DLL Redirection: Unlike the previous approach in which the search order is exploited, attackers use DLL redirection to change the search order itself. This method consists of changing the locations where the operating system searches for the DLL file. For example, the attacker can modify the registry or the PATH environment variable.
Identifying Missing DLL Files
Let's look at an example of a Phantom DLL Hijacking. To perform this attack, we would first need to identify the missing DLL files that applications are attempting to load. To achieve this, we can use a tool like ProcMon (Process Monitor).
Using this tool, you can filter events where a DLL file was not found.
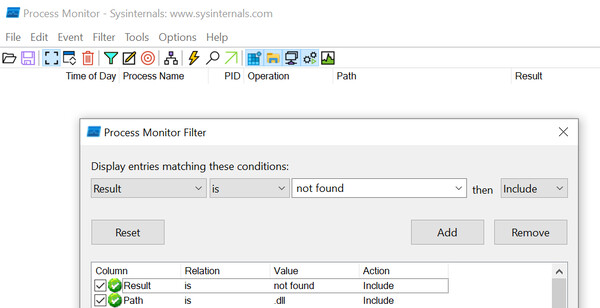
For privilege escalation, you should add another filter to only include processes that are running as SYSTEM, which is the highest privilege level on Windows.
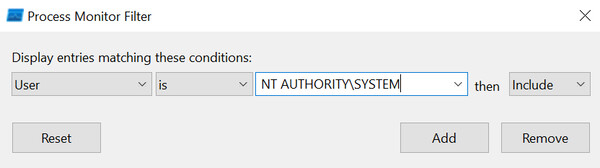
Once you identify SYSTEM processes that are calling missing DLL files, you can place your file in the location where the DLL was not found.
For the attack to be successful, you would need to have the "write" permission on the location where you want to insert your file. If that is not the case, you can always attempt to exploit the search order or perform DLL redirection as we've seen above.
Defending against DLL Hijacking attacks
Defending against DLL hijacking should start during the application development phase. Developers should specify the fully qualified path when calling DLL files to prevent the OS from searching for files in the wrong location.
Unfortunately, most programs are not developed in-house, and organizations cannot always guarantee that the programs they use are developed following certain secure coding practices. Nevertheless, they can still make sure to only use trusted software that is digitally signed, and avoid downloading software and libraries from unverified sources.
Another important control is activating the Safe DLL Search Mode. This is a registry key that restricts DLL loading. Enabling Safedllsearchmode will force the operating system to prioritize loading DLL files from system directories before attempting the local user directory.
Finally, keeping a good security posture can go a long way to protecting your organization against DLL hijacking attacks. This includes keeping your anti-malware solution up to date, performing regular scans, and raising security awareness among employees and contractors.

Comments
No comments